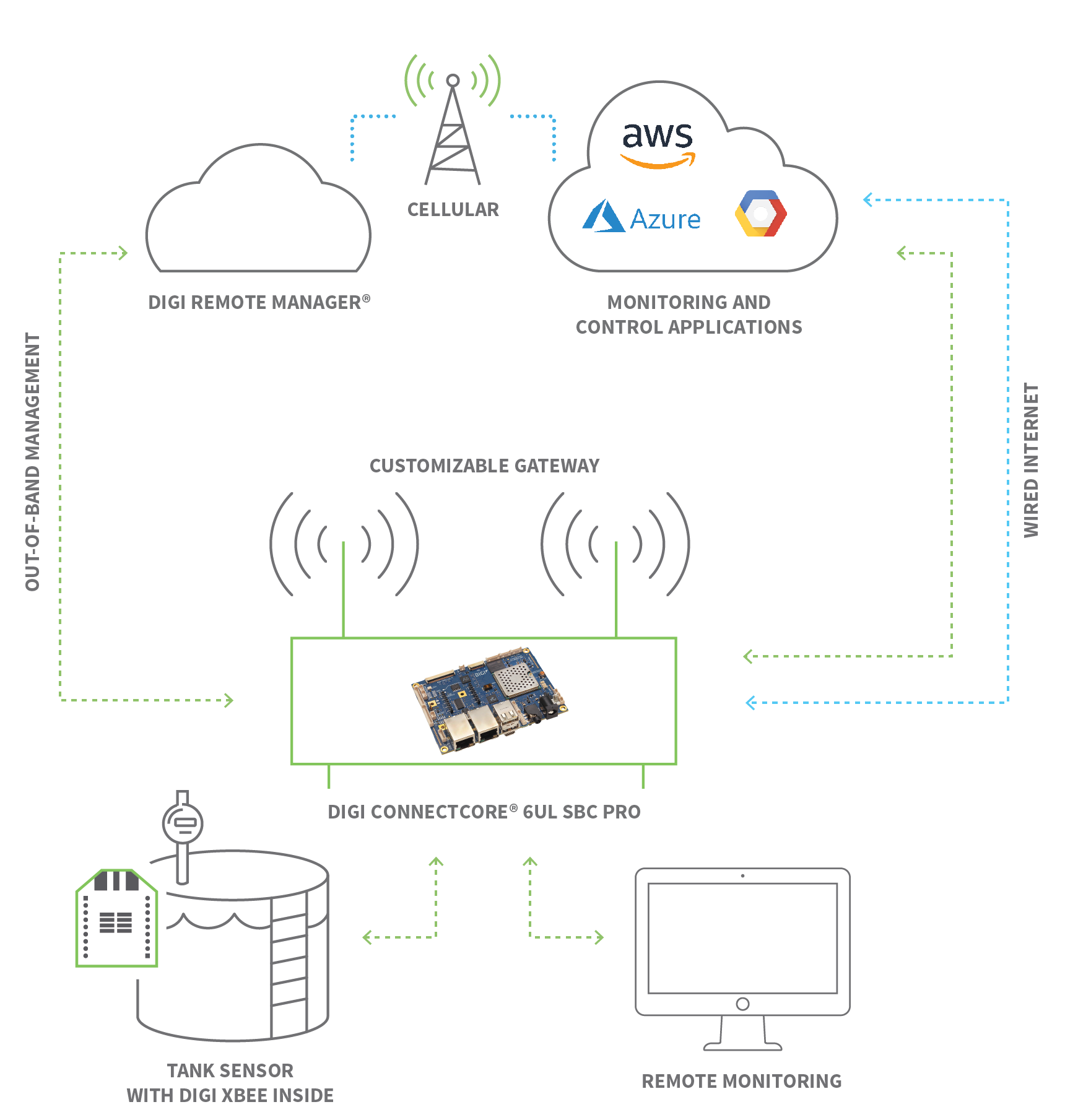
Can you truly have eyes and hands on your Internet of Things (IoT) devices, no matter where you are? The answer is a resounding yes, thanks to the power of remote access, a technology transforming how we interact with and manage our interconnected world.
Remote access to IoT devices has emerged as a critical capability, offering a multitude of advantages that extend far beyond simple convenience. It empowers users to monitor and control their devices from any location with an internet connection, providing real-time insights and the ability to react instantly to any emerging issues. This ability to act swiftly is invaluable in a world where devices are increasingly critical to daily operations, from smart home appliances to complex industrial machinery.
The core benefit lies in the ability to establish secure, reliable connections to your devices, eliminating the need for on-site visits and manual interventions. This not only saves time and resources but also minimizes downtime and maximizes productivity. It's a game-changer for businesses and individuals alike, offering a level of control and responsiveness that was previously unimaginable. With technologies like VPNs and secure tunneling protocols, you can create secure connections that protect your data and ensure the privacy of your interactions.
As the world becomes increasingly interconnected, the importance of remote access to IoT devices will only continue to grow. It is a fundamental building block for the future of device management, offering a robust and secure way to interact with our connected world.
But how does this technology work in practice? What are the underlying mechanisms that allow us to reach across distances and touch our IoT devices? Let's delve into the specific tools and techniques that make remote access a reality.
One common approach involves the use of Virtual Private Networks (VPNs). A VPN creates a secure, encrypted tunnel over the internet, allowing you to connect to your IoT device as if you were on the same local network. This method provides a high level of security and is relatively straightforward to set up. Another popular technique is the use of SSH (Secure Shell) servers, particularly on Linux-based IoT devices. By installing and configuring an SSH server, you can establish a secure connection to your device and access its command-line interface, enabling you to manage its settings, monitor its performance, and troubleshoot any issues.
For those seeking a more comprehensive solution, there are also cloud-based platforms that offer remote access and device management features. These platforms often provide a user-friendly interface, simplifying the process of connecting to and controlling your IoT devices. They may also include additional features such as remote desktop access, app control, and edge management capabilities. These features offer a holistic solution to complex IoT management scenarios.
Regardless of the specific method used, the core principle remains the same: remote access empowers you to monitor, manage, and control your IoT devices from anywhere in the world. It provides the flexibility and responsiveness needed to thrive in today's connected landscape.
The landscape of IoT device management is constantly evolving, with new tools and techniques emerging to simplify setup and enhance security. In 2023 and beyond, there are numerous solutions available to streamline the process of configuring and accessing your devices. From cloud-based platforms to traditional approaches like SSH with VPNs, the options are vast and varied.
Consider the practical applications of remote access. Imagine you're a technician who needs to troubleshoot a piece of industrial equipment located in a remote factory. With remote access, you can connect to the device, diagnose the problem, and potentially fix it without ever leaving your office. Or, imagine you're a homeowner who wants to monitor their security cameras while they're away on vacation. Remote access allows you to check on your property and ensure everything is safe and sound.
The benefits of remote access extend to all facets of IoT device management, from preventing unauthorized activity to responding immediately to any issues or adjustments needed. It provides a layer of protection, and a level of control that would be impossible without this technology.
Let's not forget the power of remote access to streamline operations. Businesses can reduce their operational costs by avoiding on-site visits. Remote access allows for proactive maintenance, as administrators can address issues before they escalate into costly failures. By analyzing data from your IoT devices, you can make data-driven decisions to optimize performance and improve efficiency.
Here is a table outlining the key advantages of remote access to IoT devices:
| Benefit | Description |
|---|---|
| Enhanced Efficiency | Streamlines operations by eliminating the need for on-site visits, reducing operational costs, and enabling proactive maintenance. |
| Improved Productivity | Enables technicians and users to instantly monitor and control their devices from any location, allowing for quick responses and adjustments. |
| Enhanced Security | Allows administrators to address unauthorized activity before any damage is done, preventing breaches and protecting against data theft. |
| Real-time Monitoring and Control | Provides continuous monitoring and immediate control of IoT devices, enabling swift responses to issues and adjustments. |
| Comprehensive Management | Features beyond traditional screen sharing, including terminal access, app control, and edge management for complex IoT management scenarios. |
| Cost Reduction | Decreases the costs associated with troubleshooting devices by eliminating on-site visits and enabling remote diagnosis and repair. |
| Data-Driven Decision Making | Provides the ability to collect and analyze data from IoT devices, allowing for optimization of performance and improvements in efficiency. |
| Global Accessibility | Offers accessibility from anywhere in the world with an internet connection, providing users with control and monitoring capabilities regardless of their location. |