Ever struggled to access and manage your Internet of Things (IoT) devices deployed in remote locations, especially when they are behind firewalls? The answer lies in AWS IoT Secure Tunneling, a powerful solution that simplifies and secures remote access to your IoT devices.
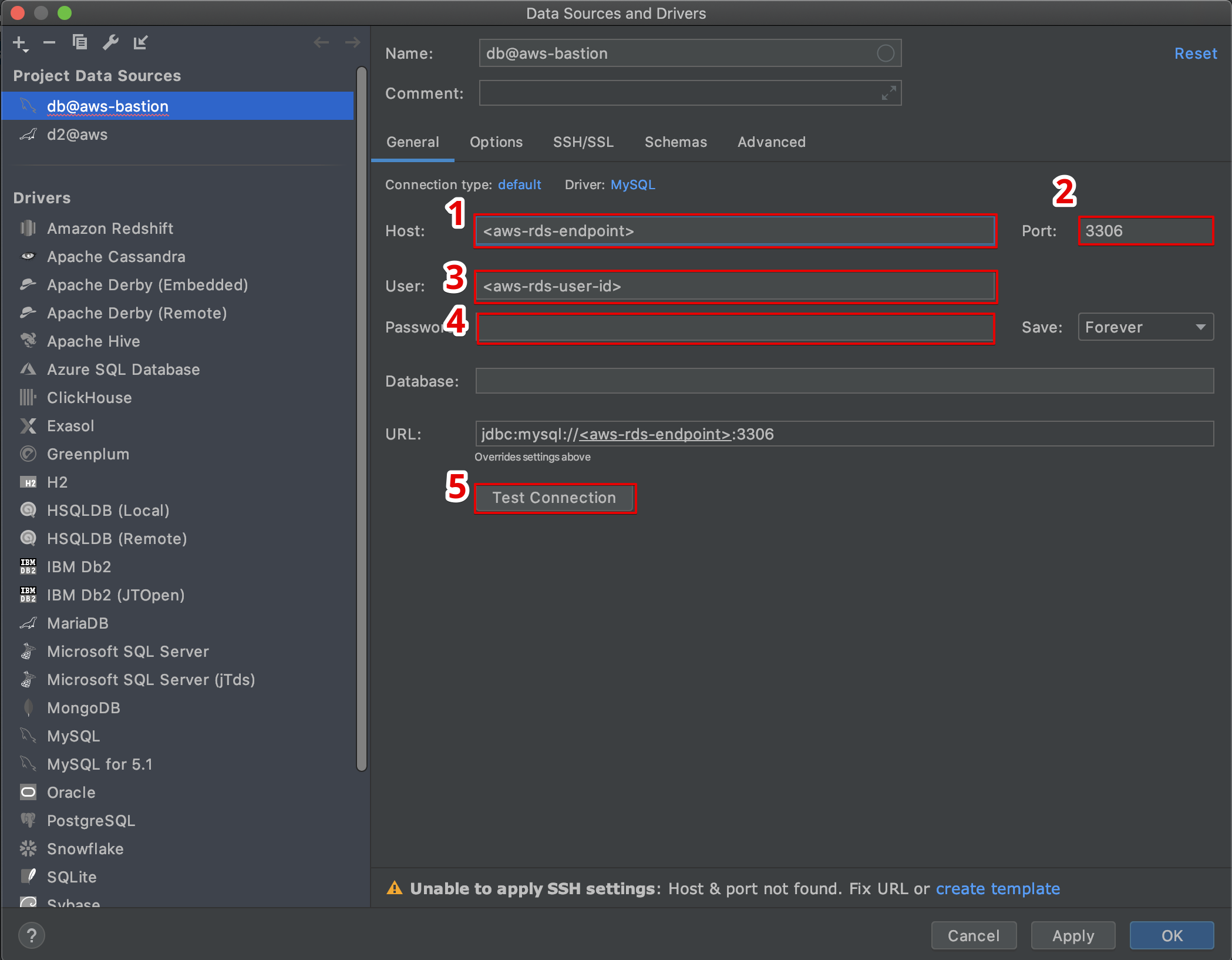
The tutorials presented in this section will serve as a guide to creating tunnels using the AWS Management Console and the AWS IoT API reference. In essence, the AWS IoT console provides a user-friendly environment where you can establish a tunnel either from the "Tunnels hub" page or from the details page of a specific "thing" (a representation of your IoT device) that you have created. Furthermore, you have the option to delete individual or multiple tunnels directly from the AWS IoT console by navigating to the "Tunnels hub," selecting the tunnels you wish to remove, and then choosing the "Delete tunnel" option. Alternatively, using the AWS IoT API reference, you can delete tunnels using the "CloseTunnel" API operation. These tools empower you with granular control over your secure connections.
| Topic: | AWS IoT Secure Tunneling |
| Purpose: | Facilitates secure remote access to IoT devices. |
| Key Features: |
|
| Benefits: |
|
| Implementation: |
|
| Considerations: |
|
| Relevant AWS Services: |
|
| Reference Website: | AWS IoT Secure Tunneling Documentation |
Firewalls, while essential for security, often create barriers to remote device access and management. The conventional approach of dispatching technicians to the device location for troubleshooting or updates is time-consuming and costly. AWS IoT Secure Tunneling provides a streamlined solution by establishing secure SSH connections to your devices, regardless of their location or network configuration. This eliminates the need to open inbound firewall ports, preserving your security posture while providing easy access.
The core of AWS IoT Secure Tunneling lies in its ability to create a secure communication pathway between two key endpoints: the source and the destination. In the context of your scenario, the source could be your AWS environment, and the destination could be your remote device. Upon successful creation of the tunnel, the system provides access tokens that are unique to each endpoint. These tokens ensure secure authentication and facilitate a trusted communication channel. The process leverages MQTT, enabling an IoT application to connect to the AWS IoT Device Gateway and listen for new tunnel notifications. The use of a software proxy that runs on both the source and destination devices is critical. This proxy relays data streams between the secure tunneling service and your device application. After the tunnel is open, AWS IoT Device Management provides the necessary configuration file, or "cat," for the source. You can download this file on the source device to activate the local proxy in source mode, effectively linking the source side of the tunnel.
To get started, tutorials will guide you through establishing a tunnel using the AWS Management Console. You can initiate this process either from the "Tunnels hub" or from the detailed view of the "thing" representing your device. This flexibility allows you to manage tunnels either on a global level or device-specifically. The "Quick setup" feature provides a simplified approach to get up and running fast. Moreover, you will learn how to delete individual or multiple tunnels. You can manage these actions from the "Tunnels hub" by selecting the desired tunnels and choosing the "Delete tunnel" action. Alternatively, the "CloseTunnel" API operation via the AWS IoT API reference offers a programmatic way to manage your tunnels.
It's important to note that the system supports "private key" SSH authentication, allowing you to easily monitor device anomalies, take immediate corrective action, and rectify the state of your devices when necessary. This feature simplifies the user onboarding process significantly, as it eliminates the need for customers to compile and install local proxies on their operator devices.
For those familiar with the basics, AWS IoT Secure Tunneling enables bidirectional communication with your remote devices over a secure connection that is fully managed by AWS IoT. The beauty of this approach is that it does not require modifications to your existing inbound firewall rules, maintaining the security level you have established at your remote site. If you have a remote device named "remotedevice1," created using the manual setup method or the AWS IoT API, the system allows you to establish a tunnel.
A deeper dive into SSH tunneling reveals that the core process creates a secure connection between two main endpoints: the source and destination. Once the tunnel is successfully established, users receive unique access tokens to facilitate secure authentication between the communicating ends.
While the process offers significant convenience, it's important to use secure practices. You can create a secure tunnel over MQTT and log in via username and password. However, if you choose to use private key authentication, it is important to ensure that the correct keys are configured on both sides. Double-check your private key and confirm that the public key is correctly set in the ".ssh/authorized_keys" file on the destination device.
In the AWS IoT console, you can navigate to the "Tunnels hub" and select a tunnel to view its details. Here, you can expand the "secure shell (ssh)" section and select "connect." If you decide to create a tunnel from the Tunnels hub, you can choose between the "Quick setup" or the "manual setup" to create the tunnel.
AWS IoT Device Management provides a range of tools that help businesses build IoT applications across various industries. However, traditionally, remote access often involves sending a control message through an MQTT topic or updating the device's shadow. With AWS IoT Secure Tunneling, these methods are streamlined to establish secure connections for device management.
To ensure optimal performance, implement best practices to maximize the effectiveness of your AWS IoT SSH tunnel, which includes using strong passwords and SSH keys to protect your devices, and never using default credentials, as they are easily compromised.
The quick setup method lets you quickly route access tokens and SSH access within your browser to the remote device. To accomplish this, it is important that you already have an IoT "thing" registered within AWS IoT.
The core functionality of AWS IoT Secure Tunneling involves a software proxy running on both the source and destination devices, which relays the data stream between secure tunneling and the specific device application. After the tunnel has been opened, the AWS IoT device management provides the "cat" or configuration file for the source, which you can download on the source device. Then you can start the local proxy in source mode, connecting the source side of the tunnel.
The approach involves establishing a secure and reliable connection between your IoT devices and the cloud. It uses SSH tunneling, one of the most effective methods to achieve this, thus enhancing your IoT infrastructure's security.
For example, to initiate a remote device, remotedevice1, and log in, you must start localproxy in destination mode and use the integration within the AWS Management Console's secure shell (SSH) to connect and log in to your device.