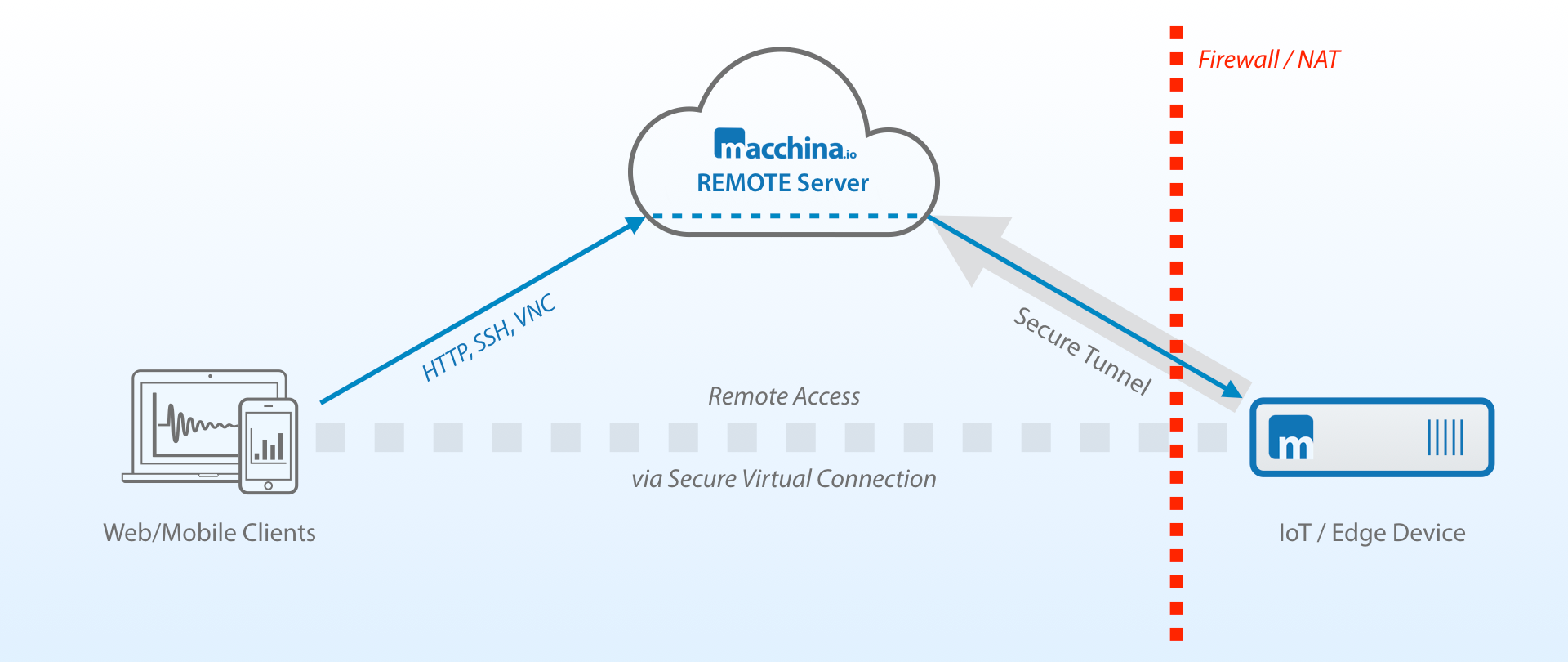
Can you imagine a world where you can manage and control your smart devices from anywhere, at any time, using just your Mac? With the power of SSH (Secure Shell) and a few simple steps, this isn't just a futuristic fantasy it's a readily achievable reality, and it won't cost you a dime.
The Internet of Things (IoT) has exploded in recent years, transforming homes, offices, and even entire cities into interconnected networks of intelligent devices. From smart thermostats and security cameras to industrial sensors and automated machinery, the potential applications of IoT are virtually limitless. However, as the number of connected devices grows, so does the need for efficient and secure remote management. This is where the magic of SSH comes in, offering a robust and cost-effective solution for accessing and controlling your IoT devices from your Mac, regardless of your location.
Let's delve into the fundamental aspects of remote IoT device management and explore how you can set up a secure and efficient connection using SSH on your Mac. This approach allows you to not only manage your devices but also monitor their performance, receive alerts, and even run batch jobs all from a single, centralized dashboard.
Enabling Remote Login on Your Mac
The first step towards remote IoT device management is configuring your Mac to accept incoming SSH connections. This involves enabling the "Remote Login" feature in your macOS settings. Here's a straightforward guide to get you started:
- Access System Preferences: Click the Apple icon in the top-left corner of your screen and select "System Preferences."
- Navigate to Sharing: In the System Preferences window, click on the "Sharing" icon.
- Enable Remote Login: In the Sharing pane, locate and check the box next to "Remote Login." This will activate the SSH server on your Mac.
With remote login enabled, your Mac is now ready to accept SSH connections from other devices on your network or the internet. Ensure that your Mac has a strong password set up to maintain the security of the connection. We will cover the best practices for securing your SSH connections later in the article.
Understanding SSH and Its Role in IoT Management
SSH, or Secure Shell, is an essential protocol in the realm of secure remote access. It establishes an encrypted connection between your Mac and a remote IoT device, ensuring that all data transmitted between the two is protected from eavesdropping and tampering. SSH provides a secure and reliable way to manage your devices, enabling you to perform a wide range of tasks, including:
- Accessing the Command Line: SSH allows you to connect to the command line of your IoT devices, giving you direct control over their operating systems and configurations.
- Transferring Files: You can securely transfer files between your Mac and your IoT devices using SSH.
- Running Commands Remotely: Execute commands on your IoT devices as if you were physically present, automating tasks and controlling their behavior.
- Monitoring Device Performance: SSH enables you to monitor the performance of your IoT devices, including CPU usage, memory consumption, and network traffic.
SSH operates on a client-server model. Your Mac acts as the client, initiating the connection to the SSH server running on your IoT device. The communication is secured using cryptography, ensuring the confidentiality and integrity of your data.
Connecting to a Remote IoT Device
Once you've enabled remote login on your Mac and ensured your IoT device has an SSH server running, you can establish a connection using the `ssh` command in the Terminal application. Here's how:
- Open Terminal: Launch the Terminal application on your Mac. You can find it in the "Utilities" folder within the "Applications" folder or search for it using Spotlight.
- Use the SSH Command: Type the following command, replacing `username` with the username on your IoT device and `device_ip_address` with the device's IP address or hostname:
ssh username@device_ip_address
- Enter Password: You will be prompted for the password associated with the username on your IoT device. Enter the password and press Enter. If the connection is successful, you will be logged into the device's command line.
Best Practices for SSH Remote IoT
Securing your SSH connections is paramount for protecting your IoT devices and your data. Here are some best practices to keep in mind:
- Use Strong Passwords: Always use strong, unique passwords for your IoT devices and your Mac account. Passwords should be at least 12 characters long and include a mix of uppercase and lowercase letters, numbers, and symbols.
- Enable Key-Based Authentication: Whenever possible, use SSH key-based authentication instead of passwords. This eliminates the risk of password interception and enhances security.
- Disable Password Authentication: After setting up key-based authentication, disable password authentication in your SSH server configuration to further enhance security.
- Keep Software Updated: Regularly update the operating systems and SSH software on your Mac and your IoT devices to patch security vulnerabilities.
- Monitor Logs: Regularly review your SSH server logs for suspicious activity, such as failed login attempts or unauthorized access.
- Limit Access: Restrict SSH access to only the necessary devices and networks. Use firewalls and access control lists to control which devices can connect to your SSH server.
- Change the Default SSH Port: The default SSH port is 22, which is well-known and frequently targeted by attackers. Change the SSH port on your Mac and your IoT devices to a non-standard port to make it harder for attackers to find your SSH server.
- Use Two-Factor Authentication (2FA): If your SSH server supports it, enable two-factor authentication for an extra layer of security.
Setting Up Key-Based Authentication
Key-based authentication is a much more secure way to connect to your devices. Instead of entering a password every time, you use a cryptographic key pair: a private key that you keep secret and a public key that you put on your IoT device. Here's how to set it up:
- Generate an SSH Key Pair: Open Terminal on your Mac and run the following command:
ssh-keygen -t rsa -b 4096
Follow the prompts. You can choose to set a passphrase for your private key, which adds an extra layer of security.
- Copy the Public Key to Your IoT Device: Use the `ssh-copy-id` command to copy your public key to your IoT device. Replace `username` and `device_ip_address` with your device's credentials:
ssh-copy-id username@device_ip_address
You may be prompted for your password during this process.
- Test the Connection: Try connecting to your IoT device using SSH. If the key-based authentication is set up correctly, you should be able to log in without entering a password.
By adopting these measures, you can significantly enhance the security of your SSH connections and protect your IoT devices from unauthorized access.
Alternative Tools for Remote IoT Management
While SSH is a powerful and versatile tool, other options are available for remote IoT management, especially if you prefer a graphical interface or need more advanced features. Here are a few alternatives:
- Chrome Remote Desktop: Whether you need to access your work computer from home, view a file from your home computer while traveling, or share your screen with friends or colleagues, Chrome Remote Desktop connects you to your devices using the latest web technologies.
- TeamViewer: This popular tool offers remote access and control capabilities with a user-friendly interface. It's available for various operating systems, making it easy to connect to your devices from your Mac.
- VNC (Virtual Network Computing): VNC allows you to remotely control a device's graphical user interface. You can find VNC server and client applications for macOS and most IoT devices.
- IoT Management Platforms: For more complex deployments, consider dedicated IoT management platforms that provide comprehensive device monitoring, control, and data analytics capabilities. These platforms often offer web-based dashboards and APIs for seamless integration with your existing systems.
These alternative tools provide various advantages and functionalities, allowing you to choose the option that best suits your needs.
Beyond Basic Access: Advanced IoT Management
Once you've established a secure SSH connection to your IoT devices, you can explore more advanced management techniques. Here are a few examples:
- Monitoring and Alerting: Use SSH to remotely monitor the performance of your devices, including CPU usage, memory consumption, and network traffic. Set up alerts to notify you of any unusual activity or critical events.
- Automating Tasks: Write scripts and use SSH to automate repetitive tasks, such as updating firmware, backing up data, or restarting services.
- Data Collection and Analysis: Collect data from your IoT devices and use SSH to transfer it to your Mac for analysis. Use scripting languages like Python or shell scripts to process the data and generate insights.
- Remote Troubleshooting: Use SSH to diagnose and troubleshoot issues with your IoT devices, such as connectivity problems, software bugs, or hardware failures. Access log files, run diagnostic commands, and reboot devices remotely to resolve problems.
Conclusion
Remotely monitoring cpu, memory and network usage, receive alerts based on monitored iot data and run batch jobs on devices. Connecting iot devices over the internet using ssh on a mac opens up endless possibilities for remote management and automation. Whether you're a beginner or an experienced developer, mastering this skill can significantly enhance your ability to interact with devices remotely. By following the steps outlined in this guide, you can securely manage and control your IoT devices from your Mac, enhancing your ability to interact with devices remotely and unlocking a world of possibilities for automation and control.